Table of contents Toc Icon
Table of contents Toc Icon
Cyberattacks aren’t just increasing; they’re evolving faster and becoming smarter and more dangerous every day.
Cybercriminals are now using AI to craft highly convincing phishing emails, texts, and deepfake videos, making it harder for organizations to detect fraud.
The rise of downloadable, pre-trained AI models has reshaped cybersecurity, fueling both innovation and threats.
Tools like WormGPT and FraudGPT can boost malware capabilities and automate phishing attacks.
Radware’s Cyber Threat Intelligence team has released the “Global Threat Analysis Report,” offering detailed insights into next-gen cyberattacks and how to protect your business against them.
In this article…
Let’s look into the key findings.
1. Web DDoS Attacks
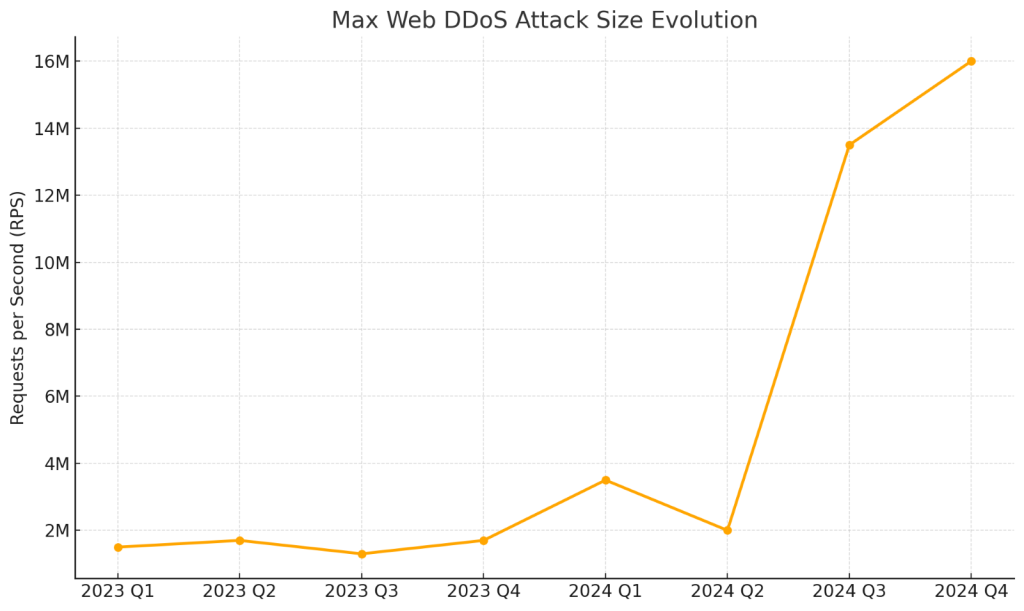
Web DDoS attacks increased by nearly 550% compared to last year. Attacks surged 246.46% in the first half of 2024 compared to the second half of 2023.
Source: Radware
Although attacks stabilized in the second half of 2024, they stayed 33.42% higher than in the first half. Web DDoS attacks may become larger and complex, leveraging AI tools and automation.
Attack intensity also grew. In 2024, 4.4% of all Web DDoS incidents exceeded 1 million requests per second (RPS), double the rate in 2023.
Meanwhile, low-intensity attacks under 50,000 RPS fell from 74% in 2023 to 66% in 2024, shifting toward more aggressive and resource-intensive assaults.
Attackers use advanced tactics like HTTP/2 Rapid Reset, Continuation Flood, and DNS amplification and will continue to use them in the upcoming years to make attacks faster and more devastating.
The barrier to entry has dropped as DDoS-for-hire services allow anyone to launch high-volume attacks for a fee.
A six-day campaign against a Middle Eastern bank peaked at 14.7 million RPS, while another financial institution faced a record 16 million RPS hit.
The Impact:
Europe, the Middle East, and Africa (EMEA) remained the primary target for Web DDoS attacks, accounting for 78% of global incidents. Organizations face longer outages, higher downtime costs, and increased difficulty identifying and mitigating threats.
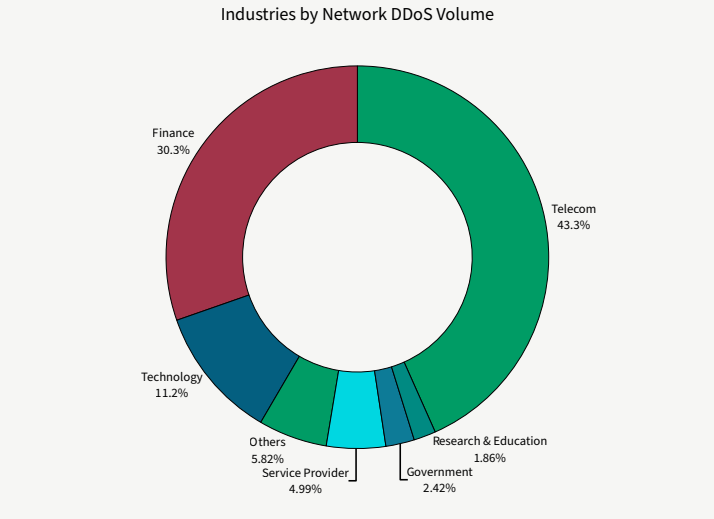
The telecommunications sector experiences the heaviest attack volumes, with over 43% of the global malicious traffic. The finance industry faced 30%, while the technology sector had 11% of the global attack volume.
Without strong defenses, businesses risk reputational damage and loss of customer trust.
The Solution:
- Implement real-time traffic monitoring to detect threats quickly.
- Deploy advanced firewalls to protect against application-layer and network-layer attacks.
- Use cloud-based DDoS mitigation services to absorb large-scale attacks.
- Apply geo-blocking where appropriate to restrict traffic from high-risk regions.
- Maintain a clear incident response plan for rapid detection and mitigation.
Protect your business with fully managed, enterprise-grade cybersecurity.
2. Hacktivism
Hacktivism drove many cyberattacks, with the number of claimed DDoS attacks on Telegram rising 20% compared to last year.
They reported 12,709 attacks in 2023, which increased to 15,295 unique claims in 2024. Attack claims posted on Telegram also frequently get forwarded to other channels.
Government institutions were the primary targets in 2024, with over 2,072 claimed attacks, followed by the e-commerce, finance, and transportation sectors.
In 2025, Telegram may become a prominent channel for attackers to exploit and steal sensitive data.
The Impact:
Due to its anonymity, bot automation, and cryptocurrency features, Telegram remains its main platform for coordination.
During the first half of 2023, India was the most targeted country.
However, in 2024, Ukraine faced over 2,000 attacks from the pro-Russia group NoName057(16), making it the top-targeted country.
NoName057(16) became the leading threat actor, with over 4,767 claims in 2024 alone and over 8,150 DDoS attack claims since January 2023.
Despite increased law enforcement cooperation and bans, Telegram’s DDoS-as-a-service bots have lowered the barrier to launching attacks.
They allow even low-skill users to cause attacks through bots that handle real-time commands, scheduling, and payments.
The Solution:
- Monitor hacktivist activity around major political events.
- Secure critical assets such as government portals and e-commerce sites.
- Use threat intelligence to track emerging alliances and attack patterns.
- Strengthen DDoS defenses against potential attacks.
- Prepare incident response teams for complex, multi-vector attacks.
- Collaborate with platforms like Telegram to stay informed on evolving threats and botnet activities.
3. Web Application and API Attacks
APIs, widely used in online services, have become prime targets for hackers and cybercriminals. According to a Cisco study, attackers shifted from the network to the application layer in 2023, causing a 171% spike in web app and API attacks, which increased 41% in 2024.
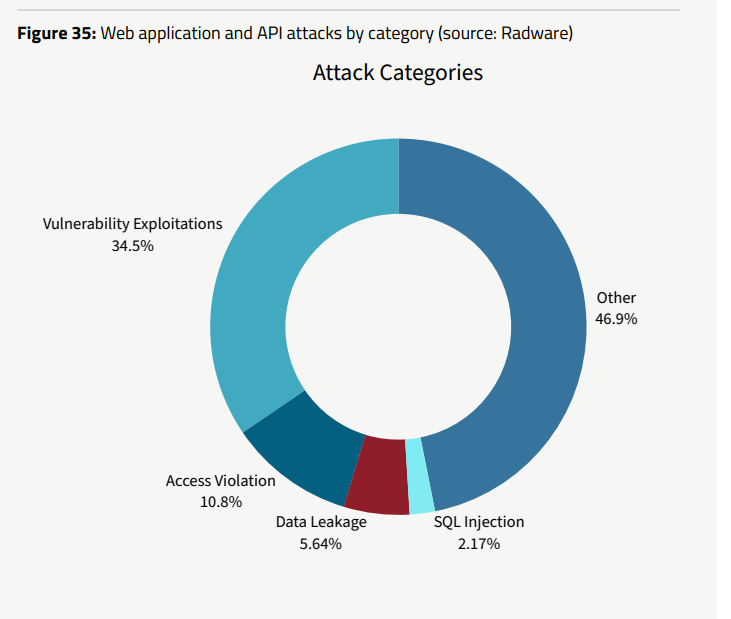
Hackers relied most on vulnerability exploitation, which accounted for 34.5%, one-third of all malicious web requests.
Access Violations (10.8%), Data Leaks, and SQL Injection attacks (2.2%) followed closely among the malicious activities. Hence, hackers may primarily exploit vulnerabilities by misusing user credentials in the upcoming year.
Predictable resource location attacks guess common files and directory names to uncover hidden web content. Attackers expose backups, configuration files, and unreleased features using automated API requests that resemble legitimate traffic, making detection difficult.
The Impact:
Unmanaged “shadow” and outdated “zombie” APIs create hidden entry points that attackers exploit to steal data or gain persistent access. These blind spots make it harder for security teams to defend systems fully.
Attackers targeted 66% of web attacks at applications and APIs in North America, with 26% hitting those in EMEA in 2024. They used advanced techniques like business logic abuse and web timing attacks, increasing the risk of serious breaches.
The Solution:
- Regularly discover and document all API endpoints, including shadow and zombie APIs.
- Implement strong authentications for all APIs.
- Continuously monitor API traffic for unusual patterns.
- Apply behavioral analytics to detect anomalies in API usage.
- Use automated vulnerability scanning and patching.
- Train security teams to understand evolving API attack techniques.
- Prioritize business logic testing to address complex API security risks before attackers exploit them.
4. Bad Bots
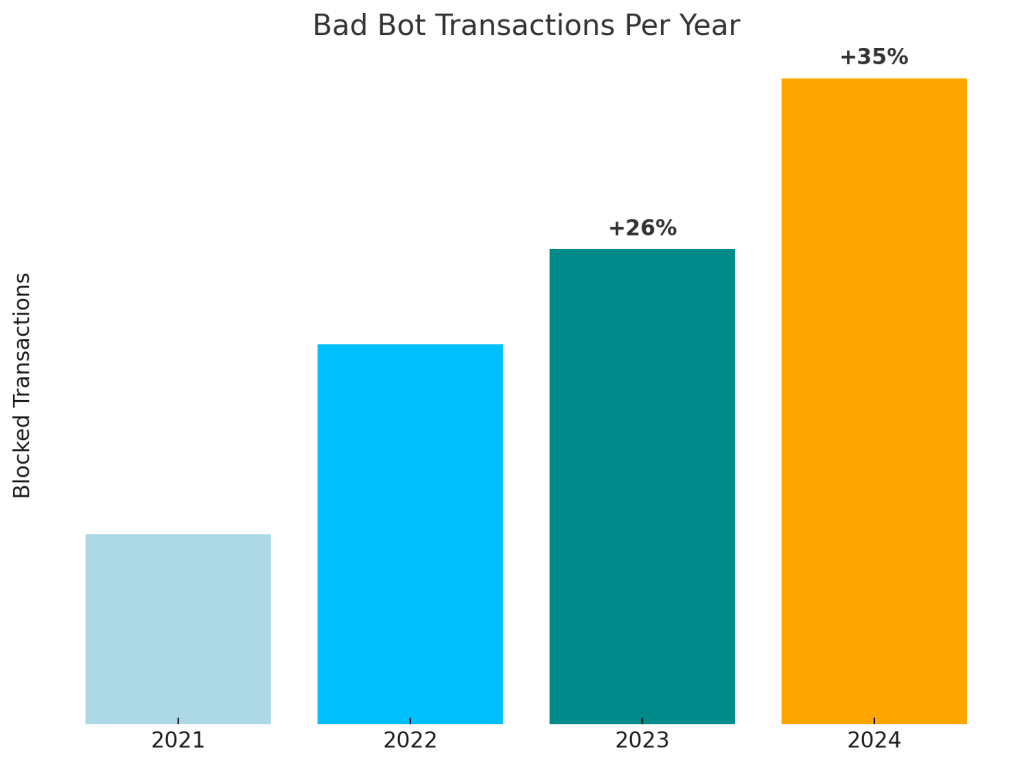
Bad bots caused 71% of all bot traffic in 2024 compared to 63% in 2023. It is driving account takeover, fraud, and data scraping, surging every year with malicious transactions.
Source: Radware
The numbers may keep rising in 2025 and the upcoming year if hackers do not stop using bad bots to steal users’ personal and payment information.
North America was the top target, with half of all malicious bot transactions. Activity peaks during high-traffic seasons like Black Friday and Cyber Monday, when attackers exploit increased online shopping and promotions.
The Impact:
Bad bots put customer accounts, sensitive data, and business revenue at risk. The rise of AI-driven “grey” bots adds complexity by scraping data to train AI models, often without permission.
Bad bot transactions jumped 35% in 2024 after rising 26% in 2023 compared to previous years. This creates challenges for organizations trying to balance protecting their data with supporting legitimate AI research and SEO efforts.
The Solution:
- Deploy advanced bot management tools to identify and block malicious bots while allowing legitimate traffic.
- Use behavioral analytics and AI-based detection to distinguish sophisticated bots from real users.
- Regularly update security policies, especially during peak traffic periods.
- Educate teams on emerging bot threats to stay ahead of evolving attack tactics.
5. Advanced Phishing and Deepfakes
77% of hackers use generative AI to create highly convincing phishing emails, texts, and deepfake videos. This makes it harder for organizations to spot fake communications. AI-driven attacks adapt quickly, testing defenses and customizing payloads faster.
The Impact:
AI tools lower the barrier for new cybercriminals, with Attackers targeting AI systems themselves. They manipulate training data or force errors, risking service reliability and data integrity and damaging brand reputation.
The Solution:
- Implement ongoing security awareness training focused on AI-driven social engineering.
- Deploy multi-layered defenses, including AI-powered detection tools for adaptive threats.
- Protect AI systems with strict data integrity controls.
- Monitor AI systems for unusual behavior or anomalies.
- Continuously invest in AI-aware cybersecurity strategies to stay ahead of evolving threats.
6. Offline AI Models
This report revealed that 71% of hackers felt AI boosted the “value” of hacking. Downloadable AI models have completely changed how cyberattacks happen. Unlike cloud-based AI with built-in controls, offline AI models are easy to access and change. Hackers use these models to create phishing scams, improve malware, and automate attacks.
The Impact:
Offline AI tools like WormGPT and FraudGPT help even less-skilled criminals to launch cyberattacks. This makes it harder for organizations to defend themselves because attacks happen faster and more often. Since no central control exists, these tools can cause big problems worldwide.
The Solution:
- Use smart security systems that can quickly detect offline AI threats.
- Continuously update threat intelligence to stay aware of evolving risks.
- Educate employees about the dangers of offline AI misuse.
- Collaborate with AI developers and regulators to prevent the abuse of offline AI models.
Don’t Let AI Outsmart Your Defense
Cyber threats are growing faster and smarter, outpacing traditional defenses. Massive DDoS attacks and sophisticated Layer 7 exploits have surpassed the reach of old protection methods. These threats impact all sectors, from finance and telecom to government and e-commerce.
Organizations must prioritize continuous risk assessment, threat intelligence, and employee training to stay ahead of various online threats.
Ace Cloud Hosting is a managed security provider with 15+ years of experience, delivering 24/7 real-time threat detection and continuous monitoring against evolving cyber threats. Book a consultation today to learn how we can safeguard your business from AI-powered attacks.
Find out if your defenses can withstand real-world threats—take the cybersecurity quiz now.






