Firewall as a Service
Combat network blindness, internet blackouts by stacking third-party cloud firewalls on Ace public cloud network branches and build surveillance-rich architecture with the PCI-DSS certified services.
Get Started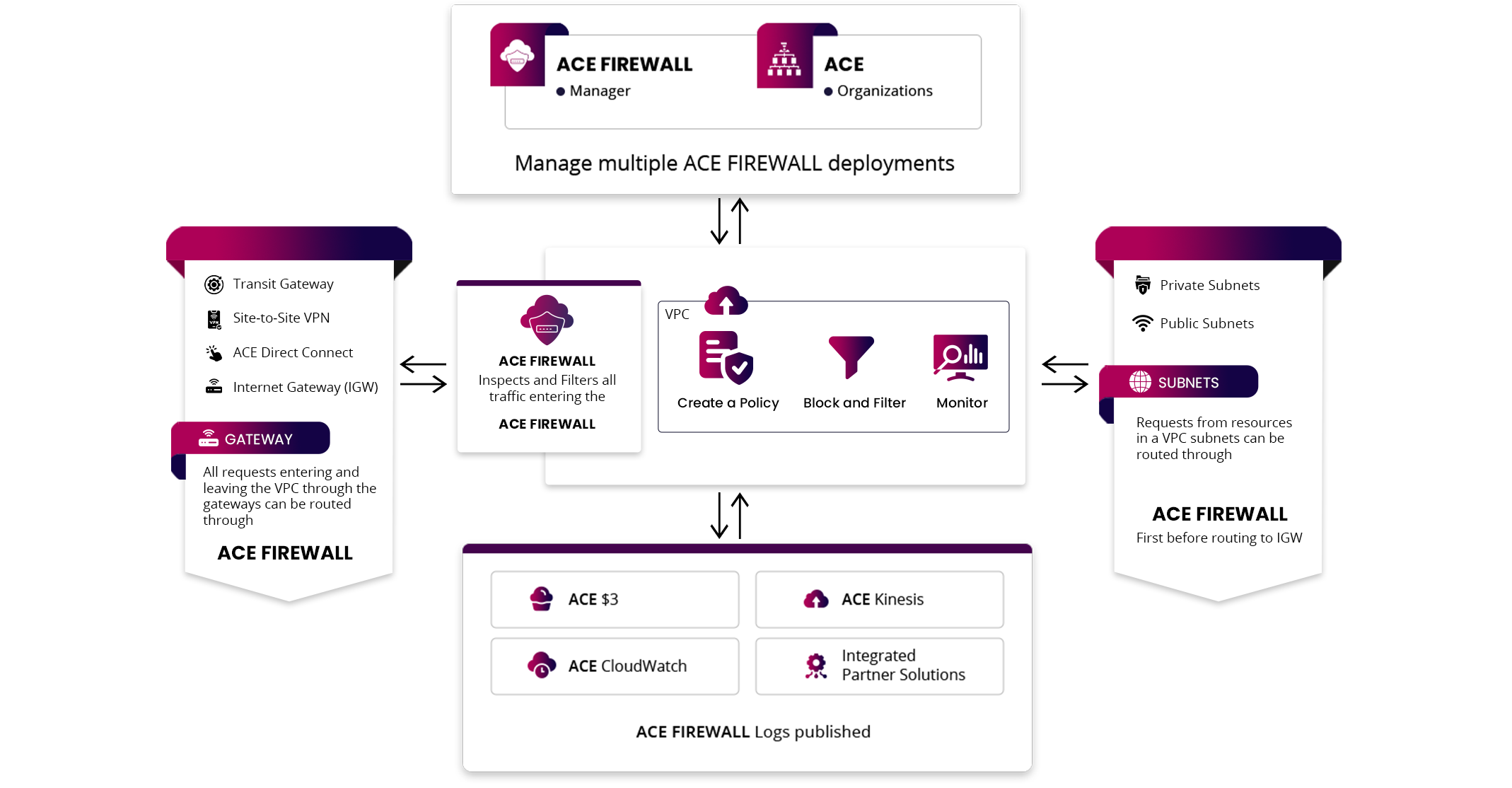

For automated network security and firewall management, Palo Alto Networks Cortex XSOAR interacts with Ace console to boost productivity and save time to detect and remediate problems

Check point CloudGuard gives Ace customers better posture management, insight, and control to evaluate misconfigurations, and rulesets including PCI-DSS, HIPAA, and NIST

Sophos integration with Ace provides premier endpoint protection, threat detection ability across trusted data sources and servers and stops ransomware attacks

You can block targeted cyberattacks, leverage remote workforce access, secure cloud adoption, distributed network security, zero-trust security, and adopt software-defined networking with SonicWall and Ace integration

Untangle in integration with Ace simplifies network security and without the hassles of many point solutions, provides you with a single, adaptable platform that suits your organization's expanding demands

Use Fortinet managed IPS rules and powerful AI capabilities to provide actionable insight and filter hazardous traffic at the perimeter in the face of an ever-changing threat scenario
Years of Exp.
Users
Data Centers
Awards
Domain Experts
Protect your network from any unwanted attack by using a cloud based IPS that protects the user from any potential threat
Procure higher control over DNS traffic by creating custom firewall rules via the intuitive Ace dashboard and protect users from reaching malicious domains
Manage data packets and use a set of policies to determine whether to allow or disallow connections to and from an application
Access granular control for both incoming and outgoing traffic to prevent DNS tunneling and data breaches
Employ FWaaS security to monitor heavy network traffic, ins and outs of data transfer and filter out malicious data
With Ace you can prevent hackers and cyber criminals from gaining unauthorized access to your data, email and organizational systems
Ace inspects and restricts traffic between network and segregates network hosting critical applications while providing fine-grained network security control
Terminate potential breaches by any malicious threat such as virus, spyware, malware from accessing your network
Create your own set of custom cloud-based firewall rules for your applications in your network and gain real-time insights to analyze your cloud network
Our firewall architecture scales elastically to protect your system and filter out threats by inspecting all the user data